Nozomi and Keysight: Visibility to Secure ICS and the Industrial Internet of Things (IIoT)
With the Internet of Things (IoT) bringing industrial operations online for the first time, network visibility and security must be extended to monitor and secure new devices. Nozomi Networks brings real-time visibility across Industrial Control System (ICS) environments with Keysight ensuring reliable access to vital data from networks and devices.
Improve ICS Cyber Resiliency
Detect, Prioritize and Resolve Threats to ICS and IIoT Infrastructures.
Nozomi Guardian uses Keysight’s visibility architecture to capture comprehensive data and eliminate network blind spots. Data gets consolidated onto a single Nozomi threat analytics platform to promote rapid incident response and proactive defense strategies. Together, Nozomi and Keysight deliver comprehensive, highly automated visibility that helps defenders respond quickly, with confidence, every time. Highlights include:
• Detect attackers in real-time to promote quick, decisive response and remediation
• Identify possible threats in ICS, IIoT, and OT environments
• Eliminate dangerous blind spots
• Continuous, automated threat detection and analysis in real time and retrospectively
Nozomi: Real-Time IT Performance and Network Traffic Analytics
Nozomi Networks delivers ICS cybersecurity solutions worldwide, providing comprehensive asset visibility, network monitoring and cybersecurity detection for industrial networks. Nozomi’s Guardian solution features a suite of application modules to visualize, monitor, detect, and take action to remediate cyber threats in real time.
The first ICS visibility solution powered by artificial intelligence (AI), Guardian offers nonintrusive visibility across ICS and SCADA (Supervisory Control and Data Acquisition) environments, including multiple geo-separated plants, without adding latency, determinism or jitter to the control network. Guardian delivers consolidated OT visibility, automatically learning all assets and working with your cybersecurity infrastructure to monitor networks and detect threats and anomalies.
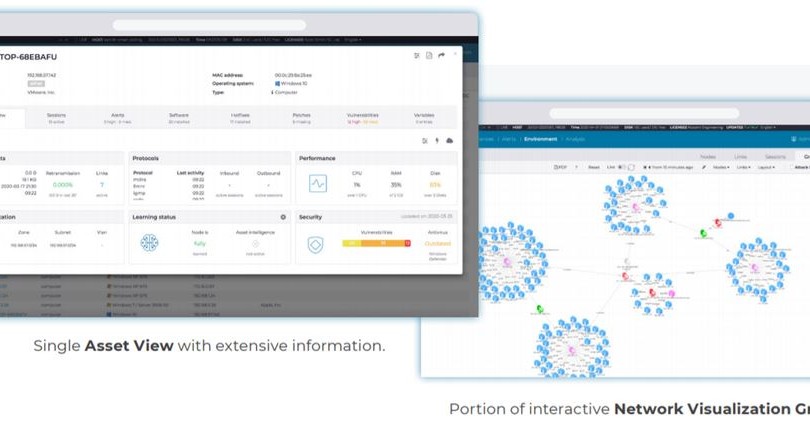
Achieve Real-Time Operational Visibility
Joint Solutions Integrating Nozomi and Keysight Technology Improve Security at Power Substations, Oil and Gas Facilities, Discrete Manufacturing Sites, and Other Remote Industrial Locations.
Together, they deliver rich contextual insight needed to defend control networks against cyberattacks, undetected failures, and costly outages.
Watch the video
Data Collection Across All of the ICS Environment
Keysight Network Visibility Solutions (NVS) deliver complete access to both OT and IT networks. Complete, real-time visibility starts with “tapping” networks to capture and copy traffic used in performance and security monitoring, incident response, forensics, and analysis. Tapping can be done in places where OT switches are not capable of adequately mirroring packets to ensure complete visibility. Taps may also substitute for data diodes since they allow copies of traffic to flow out of the monitored network segment but not back into it.
Data from the network gets forwarded to Keysight’s Visions Network Packet Brokers (NPBs) for real-time processing and delivery to Nozomi Guardian. Pre-processing of traffic includes removing duplicate packets and stripping unwanted or privileged data to improve overhead and meet compliance mandates for securing information. Vision NPBs aggregate, process, and deliver to Nozomi Guardian all relevant data from mirror and tap connections, filtering out traffic not relevant to SCADA security (such as CCTV video over IP traffic). The Vision series of packer brokers and Guardian can be integrated with security information and event management (SIEM) and other systems to establish automated threat response to indicators of compromise (IoCs). Keysight network visibility and Guardian also integrate with tools such as firewalls to improve policy enforcement and mitigate unwanted traffic.


