100% Visibility
Leverage the “Gold Standard” by providing all necessary network packets to your security and performance tools.
The demand for constant network connectivity and security is widespread. With advancing technology, challenges like edge computing, cloud environments, security threats, bandwidth needs, and compliance regulations hinder actionable insights from networks. Keysight provides solutions for rich data on network traffic, applications, and users, termed dynamic network intelligence. This aids in innovation, meeting service-level agreements, and ensuring smooth, secure application operation.
Network Taps
The Foundation of Dynamic Network Intelligence
Network taps, and the pure, unfiltered visibility into network traffic they provide, are the foundation of dynamic network intelligence. Unlike SPAN ports or port mirroring, taps provide a view of all traffic — including malformed traffic and errors that typically would get dropped. This true visibility facilitates troubleshooting, as well as security and forensics.
Keysight offers the broadest selection of taps for any network, including Flex Tap optical taps, Flex Tap Secure+ enhanced security taps, copper taps, aggregation taps, and industrial Tough Taps. For ‘virtual taps’, please see our Cloud Visibility section further down this page.

Network Packet Brokers
The Right Data for the Right Tools.
NPBs provide dynamic network intelligence by filtering, decrypting, and deduplicating traffic, optimizing tool efficiency. Keysight NPBs, unlike competitors, offer FPGA-enabled hardware acceleration crucial for mission-critical visibility deployments, ensuring full feature application at line rate without traffic loss or blind spots.

Add the Stacks That You Need
NPB feature stacks offer dynamic network intelligence that extends and enhances the functionality of an NPB with advanced packet processing
NetStack
- Includes robust filtering, load balancing, aggregation, replication, and more with three stages of filtering (ingress, dynamic, and egress) and dynamic filter compiler.
PacketStack
- Removes duplicate packets at full line rate with no loss. Other capabilities include header (protocol) stripping, packet trimming, time stamping, data masking, and burst protection.
SecureStack
- Supports inline and out-of-band SSL / TLS decryption and threat intelligence. Data Masking Plus meets
Health Insurance Portability and Accountability Act, Payment Card Industry, and other regulatory compliance requirements.
AppStack
- Provides context-aware, signature-based application-layer filtering with accurate and fast application identification, geolocation and tagging, patented signature detection, and optional RegEx filtering.
MobileStack
- Offers visibility intelligence for the mobile carrier evolved packet core with General Packet Radio Service Tunneling Protocol, or GPRS Tunneling Protocol (GTP). MobileStack provides Session Initiation Protocol correlation and load balancing, subscriber-specific filtering, subscriber allow lists, and subscriber sampling.
TradeStack
- Offers the financial capital markets a simplified market feed data management tool that removes the hassle of configuring, analyzing, and managing market feed data. Features include high-resolution traffic stats down to 0.1 millisecond resolution, microburst detection, feed health, and gap detection.
Bypass Switches
Ensure Uptime and Network Availability
External bypass switches are the key to high availability and ease of maintenance for network monitoring and security deployments. While everyone recognizes the need for tools such as intrusion prevention and firewalls, the inline deployment models of these tools can create risk or downtime when it is time for reboots, maintenance, or replacement. External bypass switches, such as Keysight iBypass, provide automated failover, which prevents tool updates or downtime from bringing down the network.

Cloud Visibility
CloudLens powers better security, visibility, and performance monitoring for the cloud
Keysight’s platform for public, private, and hybrid cloud visibility, CloudLens, enables packet capture, filtering, and analysis to provide dynamic network intelligence in any cloud environment. With its unique cloud-native architecture, CloudLens is a natural fit for cloud-only and cloud-first strategies, along with organizations that utilize multi-cloud or hybrid environments.

Visibility Central Management
Manage Many NPBs Through a Single-Pane-of-Glass.
Networks are growing increasingly complex, as is the task of extracting dynamic network intelligence information from them. Having a visibility fabric consisting of NPBs, bypass switches, and taps is a good start. What comes next is managing and coordinating all these systems. That is where Keysight’s Visibility Central Management comes in.
Centralized management enables you to manage hundreds of devices with monitoring, scheduled configuration changes, and bulk software upgrades. You can import or export configurations, run scripts, view bandwidth utilization, and more. Additionally, you can customize dashboards and integrate with other network management systems via northbound interfaces.
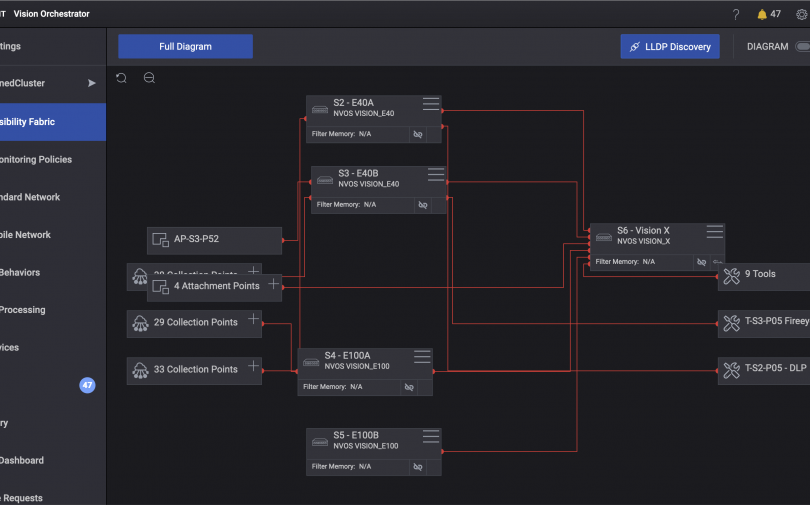
Secure Clock Synchronization
for Financial and Regulatory Compliance
TimeKeeper® is the Leading Enterprise-Class Clock Sync Platform Solution for the Financial Trading Industry.
In partnership with FSMLabs, the experts in timing technology, TimeKeeper’s innovative solutions can reliably synchronize time-critical application servers and virtual machines in data centers and hybrid cloud environments around the world to within sub-µs accuracy. This provides traceability to official time sources such as UTC and NIST.
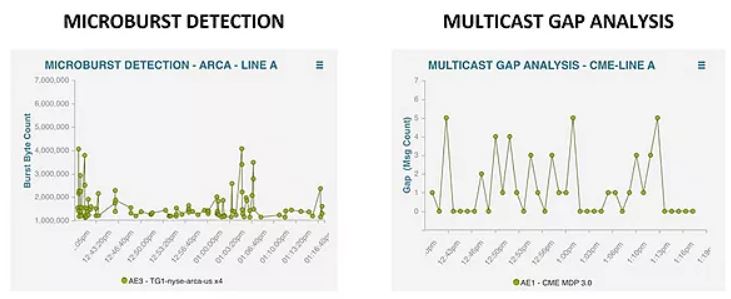
Fix Market Feed Issues Fast
TradeVision — The World’s Best High-Speed Feed Quality Monitoring Tool.
Need to monitor the quality of your market data feeds from Exchanges or market data vendors? Need to identify and fix trading issues fast? Need to plan your trading network capacity for growth? We offer the worlds leading market data aware feed monitor tool — TradeVision
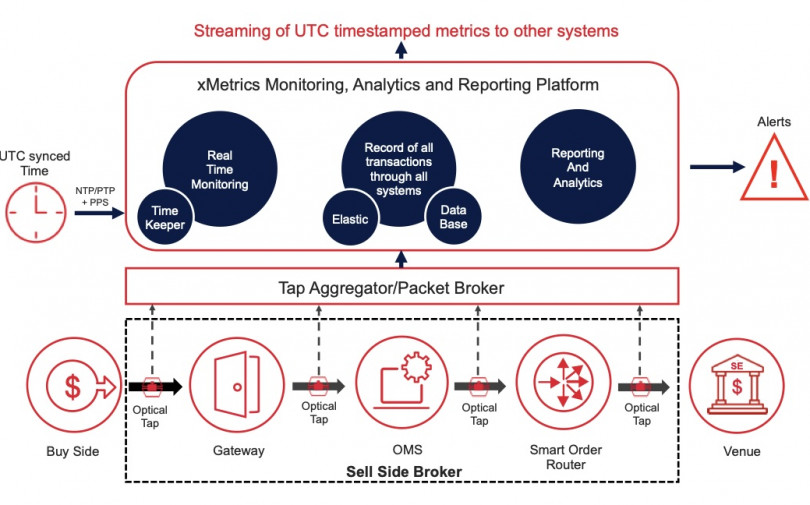
xMetrics flow monitoring software from Instrumentix
to optimize trade flow monitoring
xMetrics® runs on Vision NPBs for flawless trade flow monitoring
xMetrics flow monitoring software from Instrumentix now runs onboard Keysight Vision network packet brokers to optimize trade flow monitoring. The integration of brings first-of-its-kind real-time insight to traders, brokerages, and exchange to:
- Improve compliance.
- Improve monitoring of market data
- Reduce network, application, and trade latency
- Monitor transaction status
- Protect and analyze critical data feeds
Keysight offers xMetrics standalone or running inside Vision packet brokers for seamless, scalable financial network visibility and control. Multi-hop visibility, forensics and rich metadata accelerate analysis with affordable instrumentation and seamless integration protecting investments in legacy systems.
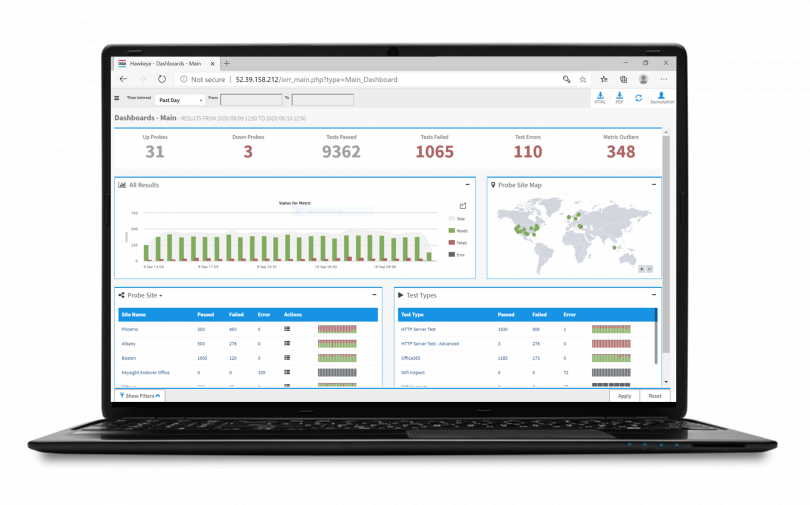
Hawkeye
Active Network Monitoring Platform
Whether you are operating your own network or a service provider delivering network services, having a reliable way to continuously verify network performance and digital experience of your end users is key toensure business continuity.
Using a combination of hardware and software agents called performance endpoints, Hawkeye simulates application traffic and sends key performance metrics to a central console for fast action. The agents provide both remote-site end-user perspectives on network performance — offering network managers a proactive way to detect, diagnose, and fix issues.
INTRODUCING
TradeVision
CATALOGS
Start Planning Today
Network Visibility Product Catalog
Build a visibility solution -network packet brokers, taps, bypass switches and more.

Network Performance and Security
Know how your network is running so you can hit tough SLAs – then secure it.
Plays well
with others
We provide data from every network segment, every type of cloud, encrypted or not, and filters at line-rate speed to increase efficiency.


