Remove Blind Spots to See Hidden Threats
Blind Spots Occur When Data is Lost on Its Way to Monitoring and Compliance Tools or Also When Security Incident Data has Become Buried
Blind spots can occur for various reasons including: overloaded SPAN ports, not using a Network Packet Broker (NPB) properly sized for your network, or lack of connectivity for tools like DLPs, SIEMs, logging tools, protocol analyzers, etc.
Network Visibility Can Help
It’s Very Common for These Blind Spots to Contribute to Network Outages, Performance Issues, and Security Breaches.
The easiest (and best) answer to solve the problem is to implement a scalable visibility architecture using external bypass switches, taps, and high-performance packet brokers.

Use Inline Security to Reduce Security Threats from Entering Your Network
Make Sure Your Security Threat Inspection Solutions Inspect All Traffic at the Entrance to Your Network.
IPS and WAF solutions can remove up to 80% or more of incoming security threats, before they ever enter your network. External bypass switches and packet brokers optimize the flow of data to those security tools as well as ensure continuous monitoring with the fastest possible recovery using a high availability configuration.
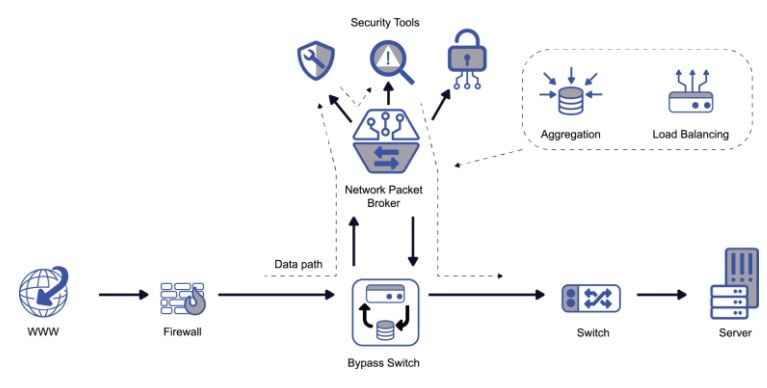
Minimize the Damage and Pain from a Security Attack with Cyber Resilience
In the Current Business Climate, It is No Longer a Question of “If” Your Network Will Be Attacked But “When”.
The real question is how quickly can you respond to the threat and recover? These are two of the fundamental questions that keep CIOs and CISOs up at night.

Use Threat Hunting to Move From Unnecessary Victim to IT Superhero
IT Security and Analytics Tools Are Only as Good as the Data They are Seeing.
Businesses need to go beyond the traditional perimeter security provided by firewalls, intrusion prevention systems, data loss prevention systems, and intrusion detection systems to actively search for threats that have infiltrated the network.
Ready to start?
Request a Live Demo
We are Here to Assist You!


