Network Performance | January 12, 2024
By Alex Rassey : Go-To-Market Strategist and Growth Leader
The Gateway to Network Efficiency
The efficient management and analysis of network data are pivotal components in safeguarding organizations against various cyber threats. For cybersecurity teams across the organization, the question of optimizing network visibility becomes paramount, and in addressing this challenge, the emergence of a crucial ally comes to the forefront – the packet broker.
From its fundamental functionalities to its transformative impact, the packet broker has evolved into an indispensable tool, enabling cybersecurity professionals to fortify their defenses in the new digital threat landscape.
Think about it this way: you can eat fries, hot dogs and hamburgers without ketchup, but for many, it makes the experience it so much better! While it is optional, when added, the entire user experience is turned way up and becomes much more enjoyable!
Understanding Packet Brokers
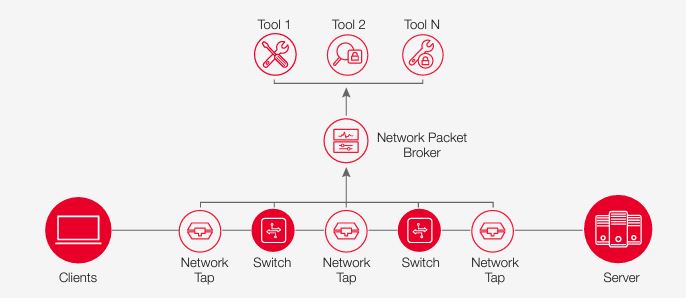
Understanding packet brokers starts with understanding traffic access points (TAPs), hardware devices that passively monitor and capture network traffic for analysis and monitoring purposes. They help to capture potentially malicious traffic at strategic points across organizations’ networks and replicate those that shouldn’t be allowed to prevent network slowdowns.
Enter the network packet broker (NPB). NPBs bring traffic from multiple sources for additional filtering to help balance traffic loads, traffic slicing, and masking capabilities. NPBs streamline the consolidation of network traffic originating from various sources, including routers, switches, and firewalls. This consolidation process creates a singular stream, simplifying the subsequent analysis and monitoring of network activities. These devices further facilitate targeted network traffic filtering, allowing organizations to focus on pertinent data for both analysis and security purposes.
In addition to their consolidation and filtering capabilities, NPBs exhibit intelligent network traffic distribution across multiple monitoring and security tools. This ensures that each tool receives the requisite data without inundating them with extraneous information. The adaptability of NPBs extends to optimizing the flow of network traffic, aligning with the unique capabilities and capacities of different monitoring and security tools. This optimization promotes the efficient utilization of resources throughout the network infrastructure.
Related Content: All You Need To Know About Your Network Packet Broker
Packet Broker Benefits
Positioned strategically between taps and SPAN ports, a Network Packet Broker (NPB) acts as a conduit to sophisticated security and monitoring tools within data centers. True to its name, the NPB serves as a broker for network packet data, ensuring optimal performance for each analysis tool. This layer of intelligence contributes significantly to cost reduction and operational simplification, yielding the following advantages:
Enhanced Decision-Making:
- A network of packet brokers equipped with advanced data manipulation capabilities organizes and streamlines data for monitoring, performance, and security tools, fostering better decision-making.
Heightened Security:
- NPBs play a crucial role in threat prevention by ensuring that firewalls, IPSs, and other defenses consistently receive the precise data they require, enhancing the overall security posture.
Accelerated Problem Resolution:
- Acknowledging the challenge posed by problem identification, NPBs with data manipulation features expedite issue detection and root cause determination. This advanced application intelligence reduces mean time to repair (MTTR), addressing the critical aspect of downtime as a cost-saving measure.
Partner Content: Check out Palo Alto Network’s Network Packet Broker Overview
Keeping Network Data Secure
Security remains a paramount focus for IT organizations as they are responsible for preventing unauthorized access to sensitive data. Simultaneously, they are tasked with ensuring that authorized users have seamless access to the pertinent information. Network Packet Brokers (NPBs) play a pivotal role in this landscape by seamlessly integrating into network security systems, such as TACACS+. This integration empowers administrators to define access permissions for users and groups meticulously.
The fine-grained access control capabilities of NPBs enable administrators to specify which groups or users have access to network data and the precise actions they are authorized to perform. This includes nuanced permissions such as modifying port settings, managing data flow connections, and defining filters. This level of control ensures a robust and tailored security framework, allowing organizations to safeguard their data against unauthorized access while facilitating legitimate users with the appropriate levels of access.
Packet Brokers optimize overall network performance by consolidating and intelligently distributing network traffic, ensuring that monitoring and security tools receive the required data, enhancing their efficacy.
Simultaneously, these brokers play a pivotal role in maintaining robust security protocols by facilitating fine-grained access control, allowing businesses to define and regulate who has access to critical network data. The result is a harmonious synergy between heightened network efficiency and fortified security measures, empowering enterprises to navigate the complexities of the digital landscape with confidence and resilience.
We know the world of TAPs and NPBs can be a little intimidating at first, but we also know they make a critical contribution to network visibility and overall cybersecurity. That’s why Get Network Visibility partners with some of the best cybersecurity service providers across all industries to enhance their products and services with our TAPs and NPBs. On top of that, we continue to add to our library of completely free resources regarding cybersecurity best practices across the board!
Back to our analogy, remember, if you spent or made the investment for monitoring performance and/or security, much like layering on some ketchup, adding that last 10% can bring the best out of your entire experience!


